TeddyID for websites
You like TeddyID as a user and you run a site or blog? Install TeddyID on your own site and watch your users enjoy a login that is easy, fun, and secure.
We have a simple integration API. If your site or blog is built upon WordPress or Bitrix, just install the plugin. You can download the plugin from WordPress or Bitrix, or just find the plugin in the admin panel of your WordPress- or Bitrix-powered site, search by "Teddy ID" keyword.
You can also install TeddyID on your site in seconds by adding just one line of javascript on your pages. See details below 1.5 factor authentication.
Our login widget fits well with any website design. It is displayed in a layer over your site, so it doesn't require any space (see example below). Also your users don't need to leave your site to log in.
1.5 factor authentication
If you authenticate your users by username and password, you can enable them to enjoy most (but not all!) benefits of TeddyID in just a few seconds. You just need to add one line of javascript to the pages of your site with login or signup forms:
<script src="https://www.teddyid.com/js/teddypass.js" defer></script>
That's it! No programming at all. (If your site is powered by one of the popular CMS, you can install a plugin that will add this line: WordPress, Joomla, OpenCart, NetCat, AmiroCMS)
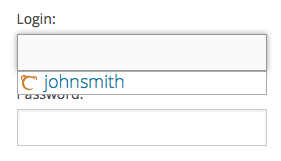
In this case TeddyID will work as a password manager for your users. When a user logs in, TeddyID will offer to save his password. When a user signs up for your site, he will be offered to generate a long unbreakable password. The passwords are saved encrypted, the encryption key is saved in the user's browser, and the password is decrypted in the user's browser only when the user wants to log in. So even Teddy never sees a user's unencrypted password.
Try it for yourself. Enter any username and password:
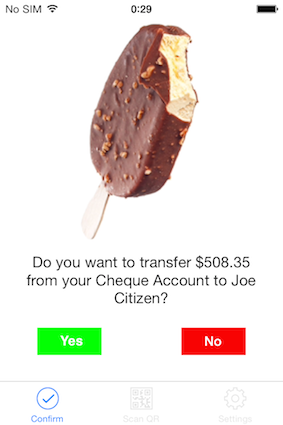
To log in to your site, the user just selects his username from the list, receives a picture to his phone, compares the pictures on the phone and on the computer, and if they match, approves the login. Having received user approval, Teddy sends the encrypted password to user's browser, the password is decrypted (with the key stored in the browser) and is filled into the login form.
As a result, the user doesn't have to remember, type, and even know his password. He just compares pictures and taps one button to log in. This will work even if he logs in to your site from different computers or browsers.
Your users will enjoy Teddy ID's ease of use. With this integration method the security level is lower than if you were to do a full integration with our API but security is still higher than with passwords. That's why we call this authentication method "1.5 factor".
| Threat | Password | 1.5 factor authentication (TeddyID Password Manager) | Integration with Teddy API or plugins |
|---|---|---|---|
| Brute force | Vulnerable | Protected Users can have long complex passwords without compromising ease of use |
Protected There is no password |
| Use of the same password on multiple sites | Vulnerable | Protected Users can have unique passwords on different sites without compromising ease of use |
Protected There is no password |
| Someone looking at password entry "over your shoulder" | Vulnerable | Protected Password is not entered |
Protected There is no password |
| Theft of password written down on Post-It notes or in a computer text file | Vulnerable | Protected Password is not entered |
Protected There is no password |
| Theft of the computer with password saved in a browser | Vulnerable | Protected Password is not stored in plaintext; encrypted password and encryption key are stored at different locations |
Protected There is no password |
| Password theft with phishing | Vulnerable | Protected Password is not entered; Teddy will not recognize bogus site since it's domain name is different |
Protected There is no password |
| Password theft with keylogger | Vulnerable | Protected Password is not entered |
Protected There is no password |
| Password theft with a Trojan in the browser | Vulnerable | Vulnerable A Trojan can steal the decrypted password |
Protected There is no password |
| Password theft in transit over open networks (if your site is not SSL protected) | Vulnerable | Vulnerable Password is passed over the network as usual |
Protected There is no password |
If hackers are after your users' data or money, they will naturally attack the weakest link. That's why we recommend that sites requiring high security integrate with our API or use plugins. However, it is often the case that a login is not the ultimate protection measure, and it is more important to authorize transactions.
How much does it cost?
The base version is free. This version allows you to receive unlimited logins from smartphone users: iOS, Android, Windows Phone, and BlackBerry. You also get up to 1000 logins a month from users with old Java phones. After the 1,000th time, these older model logins will still be processed but in less user-friendly mode: the login request will not pop up on the phone automatically; our widget will prompt the user to launch TeddyID app manually, and then he will see the login request.
This pricing structure is based on our costs structure: the Java platform is the only one on which we send costly SMS messages to reach users' phones and launch the app. All other platforms need Internet connection alone.
If you want your Java phone users to always receive login requests without any additional action from their side, you need to sign a contract with us and pay a price for each login request after the 1,000th. The price depends on country and varies from $0.015 to $0.15 per login request.
Price list
| Platform: | iOS | Android | Windows Phone | BlackBerry | Java |
|---|---|---|---|---|---|
| Base version: | free no limits |
free no limits |
free no limits |
free no limits |
free up to 1000 logins a month: push thereafter: w/o push |
| Paid version: | free no limits |
free no limits |
free no limits |
free no limits |
free up to 1000 logins a month thereafter: $0.015 per login |
For financial services and other sites that require even more security, we extend the standard login sequence with these additional steps:
- Direct confirmation from the user's phone to the client's server;
- Required PIN entry for login confirmation.
In this case, you pay for each confirmation. Contact us to request a quote.